Zero-Trust: A New Era in Enterprise Security
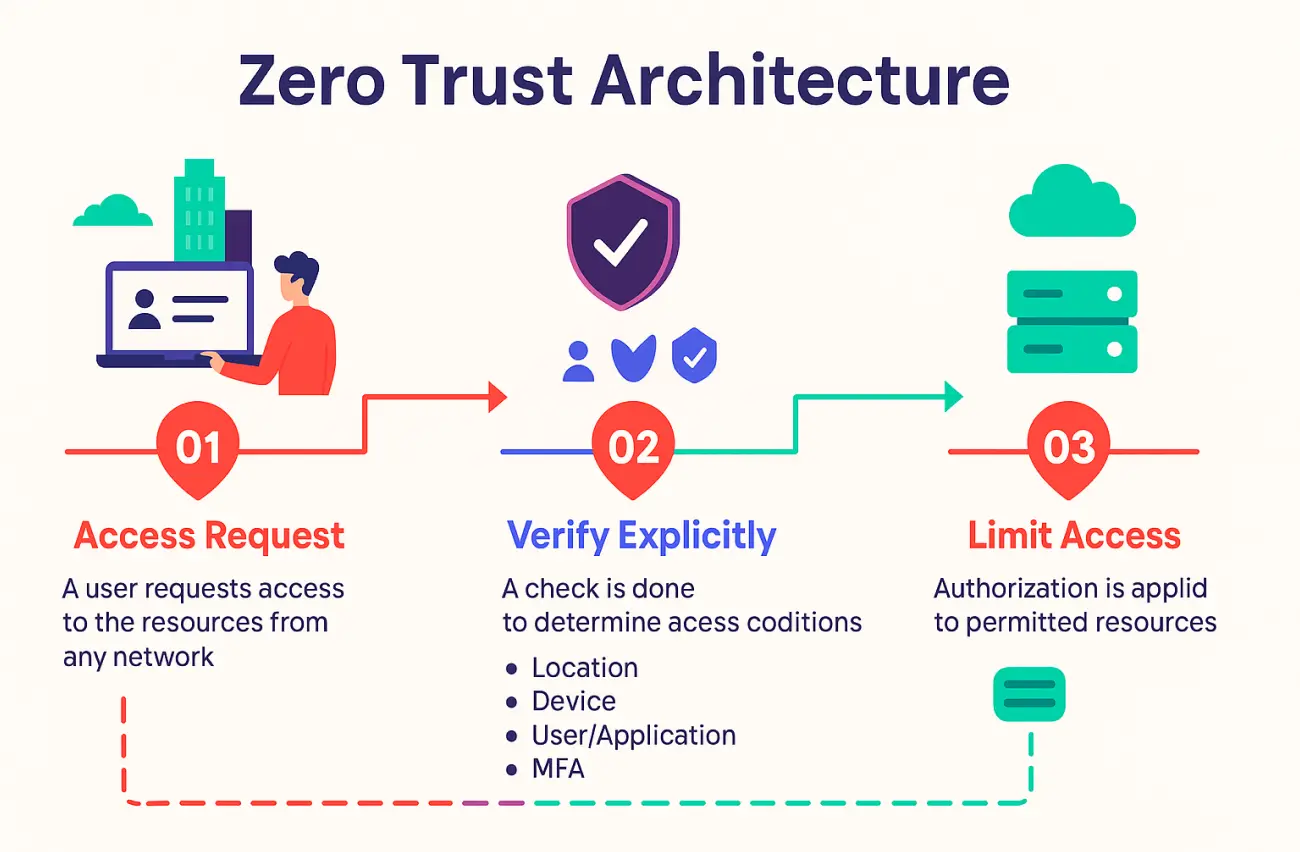
Zero-Trust Architecture (ZTA) has become essential in today’s landscape of remote work, cloud infrastructure, and evolving cyber threats. Traditional perimeter-based security models can no longer keep up. Instead, Zero Trust takes an identity-centric approach, assuming that no user or system is trustworthy by default—whether inside or outside the network.
As cybersecurity risks continue to escalate, Zero Trust has emerged as a vital framework for enterprises seeking to protect sensitive data, prevent breaches, and maintain compliance. In this insight, we break down the fundamentals of Zero Trust Architecture, explore its core components, and explain why leading organizations are making the shift now.
What is Zero-Trust Architecture?
Zero-Trust is a cybersecurity model based on the principle of “never trust, always verify.” Unlike traditional models that automatically trust users inside the network, Zero-Trust verifies every request, regardless of source.
Core Principles of Zero-Trust:
🔐 Verify Explicitly: Always authenticate and authorize based on available data (user identity, location, device status).
🛡️ Use Least Privilege Access: Grant users the minimal level of access required for their roles.
⚖️ Assume Breach: Architect systems to limit the blast radius and segment access, minimizing damage.
Why Zero-Trust Matters Now
With the rise of remote work, BYOD (Bring Your Own Device) culture, and hybrid cloud infrastructure, traditional network security is increasingly vulnerable. Cyberattacks like phishing, ransomware, and insider threats exploit outdated security assumptions.
Zero-Trust mitigates these risks by ensuring that no device or user gets automatic access, and that every interaction is authenticated and monitored.
Business Benefits:
🔒 Enhanced protection against insider and external threats
✅ Better compliance with frameworks like NIST, GDPR, HIPAA
⏳ Reduced incident response time and data breach impact
🚀 Improved agility for remote and hybrid work environments
Key Components of Zero-Trust Architecture
1. Identity & Access Management (IAM)
Robust IAM is foundational. This includes multi-factor authentication (MFA), single sign-on (SSO), and adaptive access controls.
2. Device Trust & Posture Assessment
Devices must meet predefined security conditions before gaining access. Endpoint Detection and Response (EDR) tools help monitor and assess device health.
3. Micro-Segmentation
Divide the network into secure zones to prevent lateral movement of attackers. Access to each zone is controlled independently.
4. Continuous Monitoring & Analytics
Real-time user behavior analytics (UBA) and Security Information and Event Management (SIEM) systems track anomalies and alert on suspicious behavior.
5. Data Encryption & Protection
Encrypt data at rest and in transit, and enforce policies that restrict data access based on context.
How to Implement Zero-Trust in Your Organization
- Assess Your Current Security Posture – Identify vulnerabilities and legacy systems.
- Define Your Protection Surface – Prioritize what you need to protect (e.g., data, apps, users).
- Establish Strong Identity Controls – Enforce MFA, passwordless auth, and role-based access.
- Segment Networks Strategically – Use firewalls, VLANs, and software-defined perimeters.
- Deploy Monitoring & Response Tools – Invest in SIEM, UBA, and EDR solutions.
- Iterate and Optimize – Zero-Trust is not one-time. Regularly audit, test, and improve policies.
How MarkupChop Helps
MarkupChop helps organizations design and implement Zero-Trust Architecture with:
🌐 Zero-Trust readiness assessments
🛡️ IAM and access control deployment
🕵️♂️ Real-time monitoring and anomaly detection
🏢 Micro-segmentation and policy enforcement
Want to strengthen your enterprise cybersecurity posture?
📩 Contact Us or Consult Our Expertise to start your Zero-Trust journey.
Stay Ahead with MarkupChop Insights
Explore more cybersecurity strategies and digital innovation insights at our Insights Hub